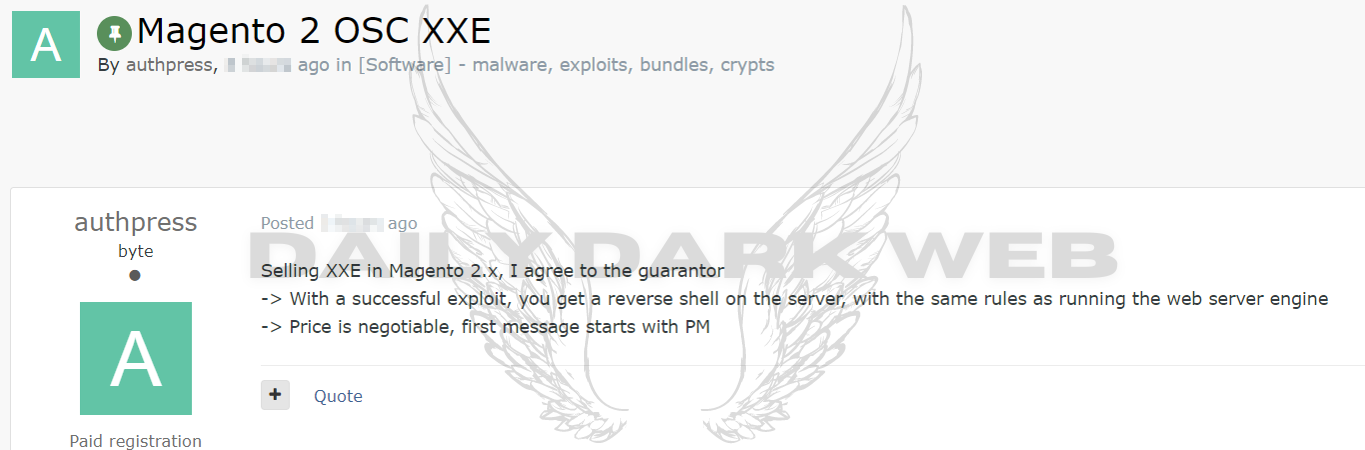
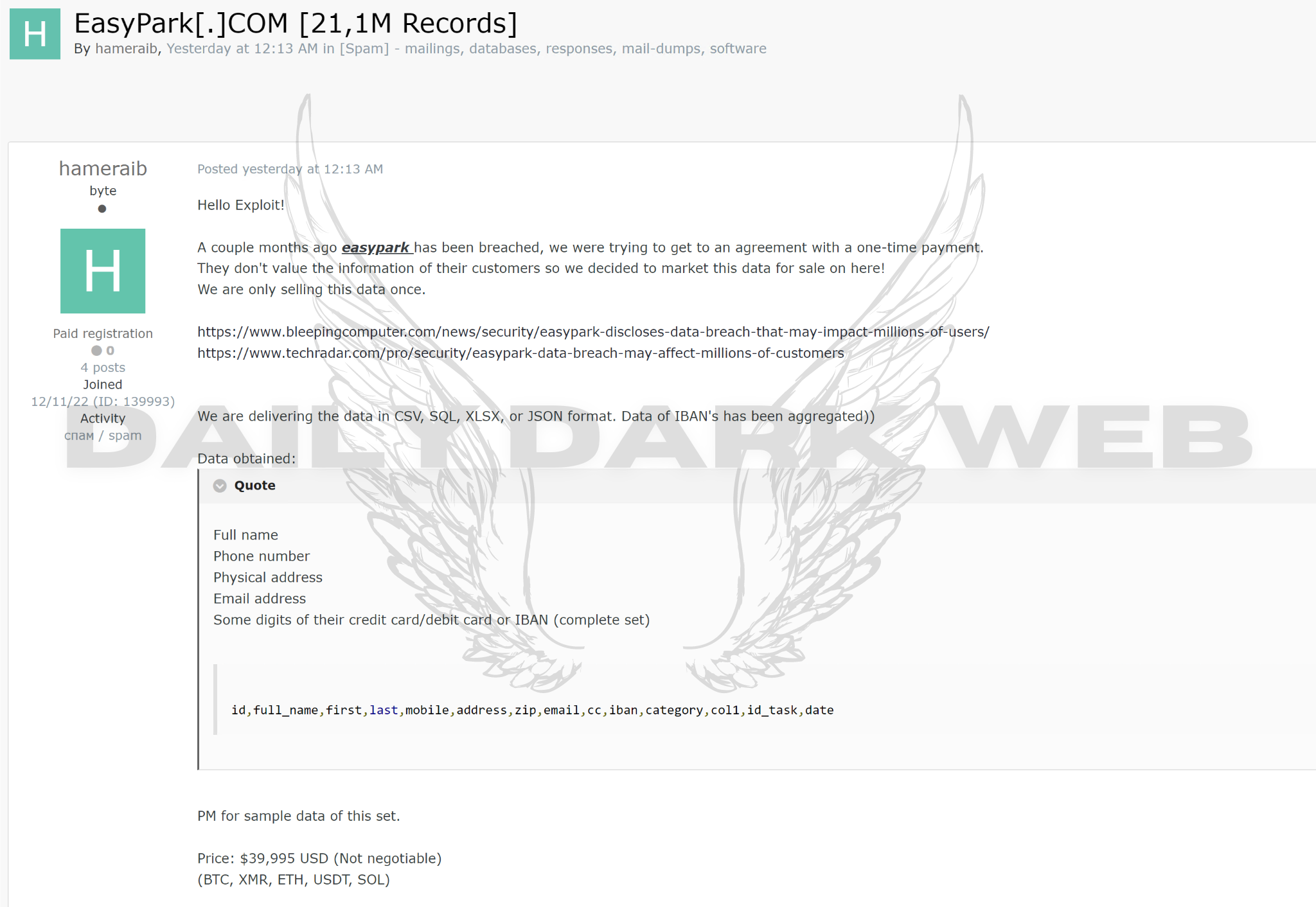
An alleged exploit targeting Magento 2 OSC has surfaced on a dark web forum, purportedly offered for sale by a threat actor. This exploit, known as XXE (XML External Entity), is touted to enable the threat actor to execute a reverse shell on the server, potentially granting unauthorized access and control.
Magento 2 One Step Checkout (OSC) is an extension that simplifies the checkout process for customers on Magento 2-based e-commerce websites. It condenses the multi-step default checkout process into a single, streamlined page, allowing customers to complete their purchases quickly and efficiently.
The price for this exploit ranges between $100,000 and $1,000,000, indicative of its perceived potency and the potential repercussions for affected systems.