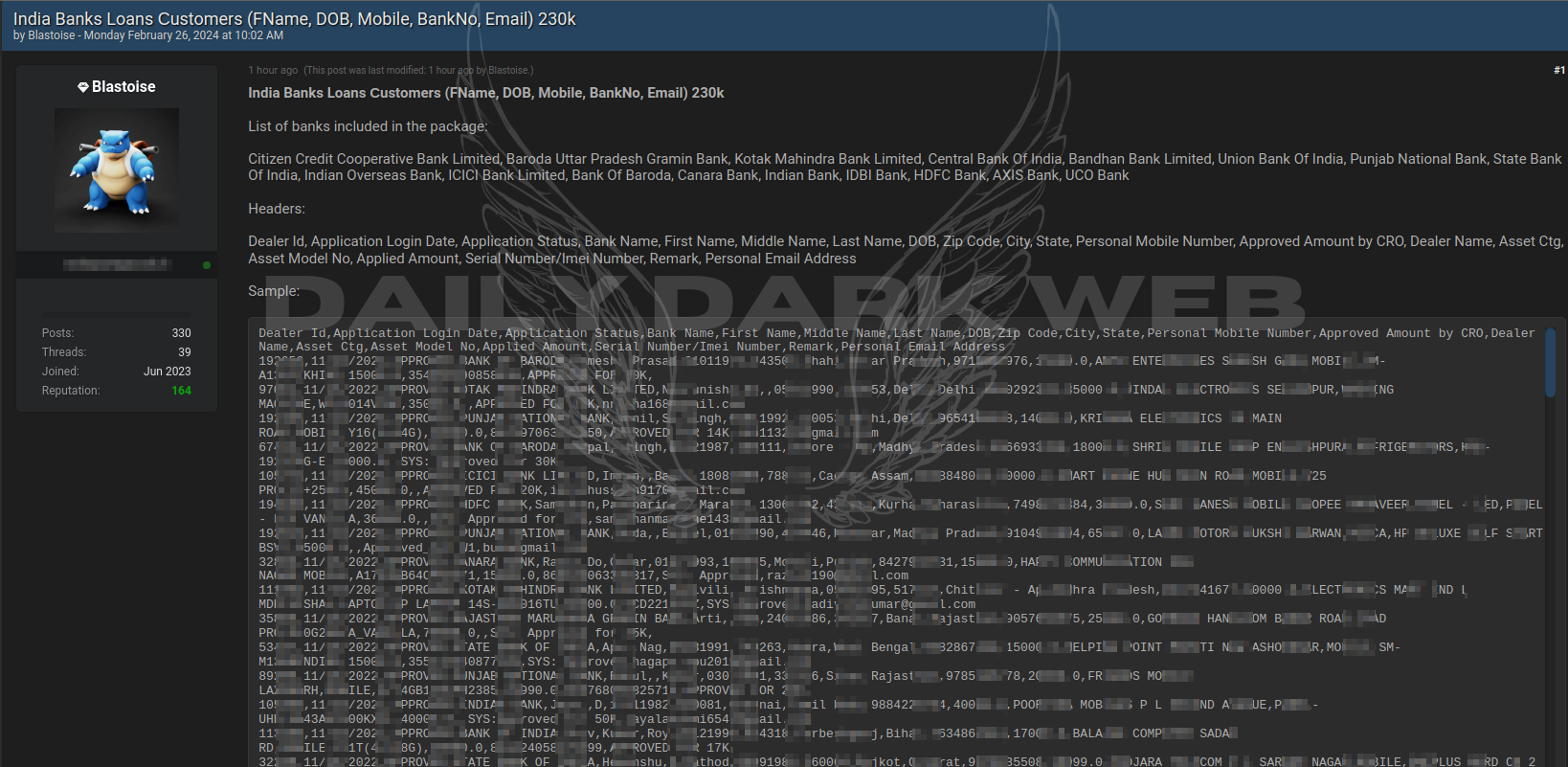
The Five Families group, notorious for its cybercriminal activities, has made a bold assertion regarding the sale of VPN access to the largest private bank in Ecuador, a financial institution with reported revenues totaling a substantial $727.2 million. This claim raises significant concerns about the security integrity of the bank’s systems and the potential for unauthorized access to sensitive financial data. The proposed price tag of $10,000 underscores the lucrative nature of such illicit activities within the cybercriminal underworld.
To prevent unauthorized access to sensitive systems and data, companies can take several proactive measures:
Implement Strong Authentication: Employ robust authentication methods, such as multi-factor authentication (MFA), to ensure that only authorized users can access critical systems and data.
Enforce Access Control Policies: Establish and enforce granular access control policies to restrict access to sensitive information based on user roles and responsibilities.
Regularly Monitor User Access: Conduct periodic reviews of user access rights to identify and revoke unnecessary privileges, reducing the risk of unauthorized access due to misconfigured permissions.
Invest in Privileged Access Management (PAM): Implement PAM solutions to monitor and control access to privileged accounts and systems, reducing the risk of unauthorized access by privileged users.
Enhance Network Security: Deploy robust network security measures, such as encryption and segmentation, to protect data in transit and contain unauthorized access attempts within distinct network zones.
Educate Employees: Provide comprehensive cybersecurity training and awareness programs to employees to help them recognize and respond to potential security threats, including phishing attempts and social engineering attacks.
Conduct Regular Security Audits: Perform periodic security audits and penetration tests to identify vulnerabilities and weaknesses in the organization’s defenses, enabling proactive remediation to prevent unauthorized access.
By implementing these proactive security measures and adopting a holistic approach to cybersecurity, companies can strengthen their defenses against potential unauthorized access attempts and safeguard their sensitive data and systems from cyber threats.