R00TK1T has purportedly breached the security of AMC University College in Malaysia, raising concerns over the safety of personal data. The group alleges to have obtained extensive personal information, encompassing names, addresses, contact details, and potentially more, belonging to both students and staff members of the educational institution.
This alleged infiltration highlights significant vulnerabilities in AMC University College’s data protection measures and underscores the urgent need for enhanced cybersecurity protocols to safeguard sensitive information and mitigate potential risks.
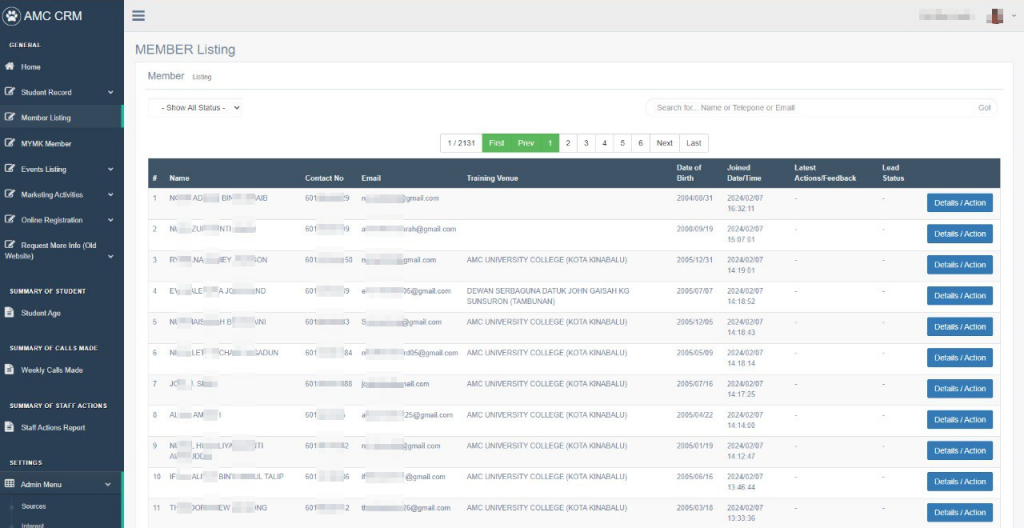
The stolen personal information from the alleged breach of AMC University College could be utilized by threat actors for various nefarious purposes, including:
- Identity Theft: With access to names, addresses, and contact details, threat actors could engage in identity theft, using the stolen information to open fraudulent accounts, apply for loans, or conduct other illicit activities in the victims’ names.
- Financial Fraud: The compromised data could be exploited to commit financial fraud, such as unauthorized transactions, money laundering, or accessing sensitive financial information.
- Phishing Attacks: Threat actors could use the stolen contact details to launch targeted phishing attacks, where victims are tricked into disclosing additional personal information, login credentials, or financial details.
- Social Engineering: Armed with personal information, threat actors could impersonate individuals to gain unauthorized access to accounts, manipulate victims into providing further sensitive information, or perpetrate social engineering attacks.
- Sale of Information: The stolen data could be sold on underground forums or dark web marketplaces to other cybercriminals for further exploitation, monetization, or identity theft purposes.
Overall, the compromised personal information poses significant risks to the privacy and security of students and staff members of AMC University College, highlighting the importance of robust cybersecurity measures and proactive action to mitigate the potential impact of such breaches.