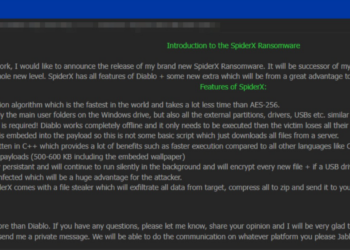
A highly alarming new type of ATM malware has emerged in Europe, boasting an unprecedented 99% success rate. Dubbed “EU ATM Malware”. This malicious software has the potential to compromise almost any ATM in Europe and approximately 60% of ATMs worldwide, posing a significant threat to global banking security. The malware is reportedly capable of targeting ATMs manufactured by leading companies such as Diebold Nixdorf, Hyosung, Oki, Bank of America, NCR, GRG, and Hitachi, among others.
The developers of this malware claim that it can generate up to $30,000 per ATM, making it a lucrative tool for cybercriminals. The malware is fully automated, simplifying its deployment and operation. However, it also includes a manual operation mode for those who prefer a hands-on approach.
The malware is being sold with flexible payment options, including:
- A monthly subscription.
- A test payload option valid for three days.
- An initial fee plus a share of the profits from successful jackpotting operations.
The European banking sector, known for its stringent security measures, now faces a formidable challenge in safeguarding its ATM infrastructure against this advanced and pervasive threat.